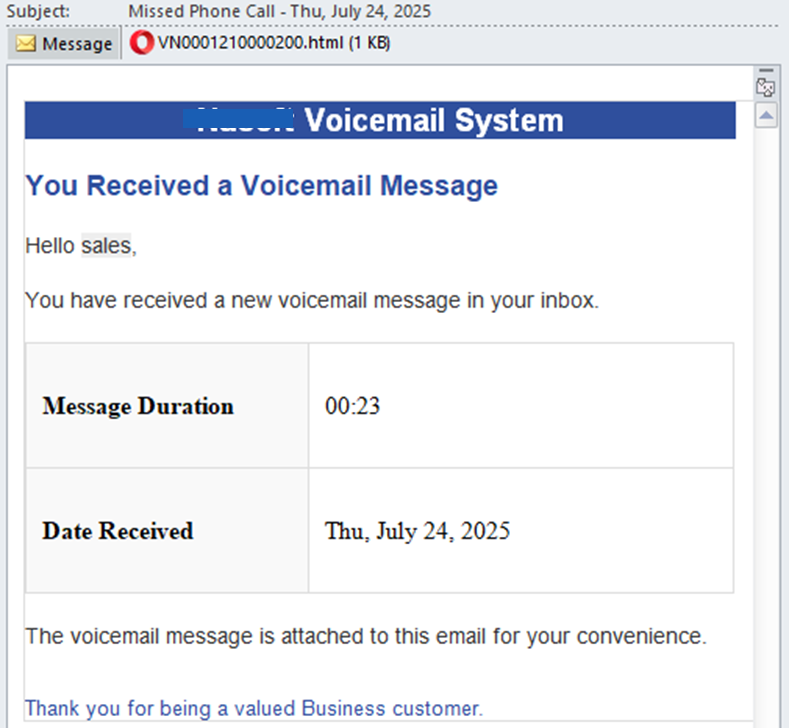
Fake Voicemail Emails Install UpCrypter Malware on Windows

FortiGuard Labs warns of a global phishing campaign that delivers UpCrypter malware, giving hackers complete control of infected Windows systems and raising serious security concerns.
A major new cybersecurity alert has been issued by FortiGuard Labs, the research division of Fortinet, following its discovery of a highly dangerous phishing campaign. The findings from this research were shared with Hackread.com ahead of its publication on August 25, 2025. The attack is designed to trick Microsoft Windows users into unknowingly installing powerful malware that can give hackers complete control over their computers.
The campaign, which FortiGuard Labs’ telemetry shows is operating on a global scale, has grown rapidly, with detections doubling in just two weeks, impacting several industries, including manufacturing, technology, healthcare, construction, retail and hospitality.
Researchers observed that this is not just a simple scam to steal login details, but a full-scale attack process that can secretly install a harmful program inside a company’s network, allowing attackers to maintain control for a long time.
The attack begins with an email, which could either pretend to be a “Missed Phone Call” or a “purchase order”. Both emails contain a malicious file disguised as an HTML attachment named, for example, “VN0001210000200.html” or “採購訂單.html“.
When opened, these files redirect the user to a fake, but very convincing, website, which even displays the victim’s own company email domain and logo to appear legitimate.
This fake page forces the victim to download a malicious file by clicking on the “download” button, after which a harmful JavaScript file is delivered. As shown in the attack flow diagram, this file then works to secretly download and install the next stage of the malware without the user’s knowledge.
Accorfing to the company’s blog post, the downloaded JavaScript file is a dropper for UpCrypter, a malware developed by Pjoao1578. Its purpose is to secretly install more dangerous tools. Researchers found that UpCrypter is being used to deploy different types of Remote Access Tools (RATs), which are programs that let an attacker remotely control an infected computer. The specific RATs identified in this campaign were DCRat, PureHVNC, and Babylon RAT.
UpCrypter is designed to be highly evasive, with sophisticated checks to see if it is being analysed by security tools like Wireshark or ANY.RUN, or running inside a virtual environment. If it detects any, it may stop its actions or even force a system restart to avoid being caught. The malware can even hide its malicious code inside a JPG image file. To ensure it continues to run, it adds a key to the Windows registry, a detail crucial to security.
Given the high severity of this threat, FortiGuard Labs urges individuals and companies to take it seriously. Organizations should use strong email filters and make sure their employees are well-trained to recognize and avoid these types of attacks.
“Various fake voicemail and fake invoice phishing lures remain popular for attackers simply because they work,“ said John Bambenek, President at Bambenek Consulting. “In this case, however, looking for the chain of events of opening an HTML attachment in email that leads to PowerShell usage provides an easy and quick win to detection (and hopefully prevent) this chain of events. Not every user needs access to PowerShell, and certainly not when the chain starts from Outlook.exe,“ he cautioned.
HackRead