New Nitrogen Ransomware Targets Financial Firms in the US, UK and Canada

Nitrogen, a ransomware strain, has emerged as a major threat to organizations worldwide, with a particular focus on the financial sector. First identified in September 2024, Nitrogen has rapidly gained notoriety for its sophisticated attack methods and devastating impact.
This ransomware encrypts critical data and demands substantial payments for decryption. It has targeted industries such as finance, construction, manufacturing, and technology, primarily in the United States, Canada, and the United Kingdom.
Cybersecurity experts warn that Nitrogen’s advanced tactics and evolving strategies pose a severe risk to organizations unprepared for its precision and persistence. The use of malware analysis and threat intelligence tools can mitigate these risks and prevent incidents.
Nitrogen’s complex attack chain begins with malvertising campaigns on search engines like Google and Bing. The ads trick users into downloading trojanized installers disguised as legitimate software, such as AnyDesk, WinSCP, or Cisco AnyConnect.
Once installed, the ransomware uses tools like Cobalt Strike and Meterpreter shells to establish persistence, move laterally within networks, and execute its payload. Nitrogen modifies registry keys and schedules tasks to ensure they remain active even after the system reboots. It conducts thorough system reconnaissance, identifies high-value targets within networks to maximise the impact, and employs advanced evasion techniques.
- SRP Federal Credit Union (USA): in December 2024 this attack introduced Nitrogen to the wider world and exposed the financial sector’s vulnerability.
- Red Barrels (Canada): the video game developer had 1.8 terabytes of sensitive data extorted, including game source codes and internal documents.
- Control Panels USA: a custom control panel solutions provider was listed as a victim on Nitrogen’s dark web leak site in September 2024, indicating a successful breach and potential data exfiltration.
- Kilgore Industries: In December 2024 the manufacturing company faced a ransomware attack attributed to the Nitrogen group.
Not much is yet known about Nitrogen modus operandi due to limited public data. The main publicly available source of information is the report by StreamScan. It offers key indicators of compromise and some insights into the methods but is light on details. This is where ANY.RUN’s experts step in, offering deeper insights through dynamic analysis and threat intelligence enrichment.
The StreamScan report details a few critical IOCs:
- Ransomware File: A malicious executable with the
SHA-256 hash 55f3725ebe01ea19ca14ab14d747a6975f9a6064ca71345219a14c47c18c88be
- Mutex: A unique identifier,
nvxkjcv7yxctvgsdfjhv6esdvsx, created by the ransomware before encryption.
- Vulnerable Driver:
truesight.sys, a legitimate but exploitable driver used to disable antivirus and endpoint detection tools.
- System Manipulation: Use of bcdedit.exe to disable Windows Safe Boot, hindering system recovery.
These indicators can be researched via Threat Intelligence Lookup to find more IOCs, behavioural data, and technical details on Nitrogen attacks.
Nitrogen creates a unique mutex to ensure only one instance of the ransomware runs at a time. Using the mutex’s name as a TI Lookup search request, one can discover over 20 related malware samples analyzed by the users of ANY.RUN’s Interactive Sandbox.
syncObjectName:”nvxkjcv7yxctvgsdfjhv6esdvsx”
For each sample, an analysis session can be explored to enrich the understanding of the threat and gather additional indicators not featured in public research. These IOCs can be used for tuning monitoring, detection and response systems to ensure proactive protection against the malware.
Nitrogen exploits truesight.sys, a legitimate driver from RogueKiller AntiRootkit, to kill AV/EDR processes and thus disable antivirus and endpoint detection tools. This driver is used by threat actors because it’s not inherently malicious, so it does not trigger standard defences. ANY.RUN’s TI Lookup reveals over 50 analyses linked to truesight.sys:
sha256:"Bfc2ef3b404294fe2fa05a8b71c7f786b58519175b7202a69fe30f45e607ff1c"
By parsing these analyses, teams see how the driver can be abused, from terminating security processes to evading detection. Searching by the driver’s name with the “CommandLine” parameter results in a selection of system events involving the driver:
Discovering such activity induces security teams to timely block the vulnerabilities of such types.
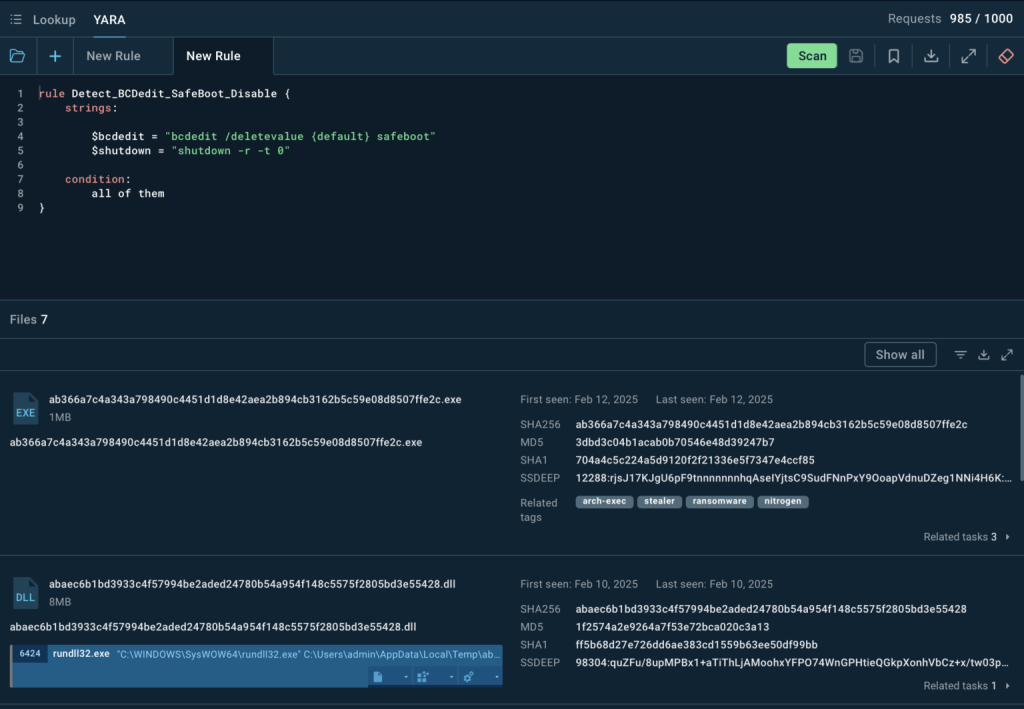
Nitrogen uses the Windows utility bcdedit.exe to disable Safe Boot, a recovery mechanism that helps restore an infected system. ANY.RUN allows analysts to use YARA rules to search for this behaviour, identifying malware that tampers with system settings.
A YARA search in TI Lookup returns several files linked to this tactic, each with an associated analysis session that reveals additional IOCs.
By integrating these IOCs into SIEM or EDR systems, organizations can detect and block attempts to modify Windows boot settings before encryption begins, stopping Nitrogen in its tracks.
To defend against threats like Nitrogen, security teams should:
- Block known malicious infrastructure and domains.
- Monitor for unusual use of PowerShell, WMI, and DLL sideloading.
- Educate employees about phishing and social engineering tactics.
- Use threat intelligence services to proactively hunt for related IOCs and TTPs.
- Use DMARC, DKIM, and SPF to prevent email spoofing, a tactic often used to deliver Nitrogen’s malicious payloads.
- Regularly update software and apply patches to close vulnerabilities exploited by Nitrogen.
In the face of growing threats like Nitrogen ransomware, real-time analysis and threat intelligence are no longer optional, they’re essential. To mark its 9th anniversary, ANY.RUN is launching a limited-time promotion to help security professionals stay ahead of modern cyber threats with the Interactive Sandbox and Threat Intelligence Lookup solutions.
Grab the gift: extra Sandbox licenses for your team, or double TI Lookup quota.
Disclosure: This article was provided by ANY.RUN. The information and analysis presented are based on their research and findings.
HackRead