Two Hacks, One Empire: The Cyber Assaults Disney Didn’t See Coming

Disney was hit by two major 2024 cyberattacks, an ex-employee’s sabotage and a hacker’s AI trap, exposing internal flaws and stealing 1.1TB of sensitive data.
In two unrelated incidents, The Walt Disney Company has found itself the target of major cyber attacks from disgruntled former employees and external malicious actors. These cases, unfolding in 2024, involve a range of damaging activities, from menu sabotage to large-scale theft of confidential data.
One of these incidents involved Michael Scheuer, a former menu production manager at Walt Disney World. Following his termination for misconduct in June 2024, Scheuer launched a digital campaign of sabotage against his former employer. He illegally accessed Disney‘s internal menu creation system for park restaurants and made dangerous alterations.
These included falsely labelling food items containing peanuts as “peanut-free,” a change that could have had life-threatening consequences for individuals with peanut allergies. Strangely, Scheuer’s VPN IP address range matched his usage while employed, which should have been terminated.
Furthermore, Scheuer tampered with wine region labels, referencing locations of recent mass shootings, altered prices, inserted offensive language, replaced QR codes with links to a website advocating for a boycott of Israel due to the Gaza invasion, and even changed the menu font to the symbolic Wingdings typeface, rendering the system inoperable. Fortunately, Disney detected these changes before they impacted customers.
Scheuer also deployed a bot designed to repeatedly attempt logins to at least 14 employee accounts, effectively rendering their accounts unusable. A “dox” folder found on his computer contained the personally identifiable information (PII) of his targets, indicating an intent to intimidate/harass them. Arrested in October 2024, Scheuer pleaded guilty and expressed remorse. Prosecutors advocated for a 70-month prison sentence, but Scheuer was sentenced to three years and ordered to pay nearly $688,000 in restitution.
In a separate incident, a California resident Ryan Mitchell Kramer, 25, under the alias NullBulge, pleaded guilty to “one count of accessing a computer and obtaining information and one count of threatening to damage a protected computer” for hacking a Disney employee.
For your information, Kramer hacked a Disney employee by distributing a malicious AI image generation tool extension on GitHub in April 2024, as reported by Hackread.com. This fake extension, ComfyUI_LLMVISION, stole passwords and payment data, sending it to Kramer’s Discord server, revealed vpnMentor.
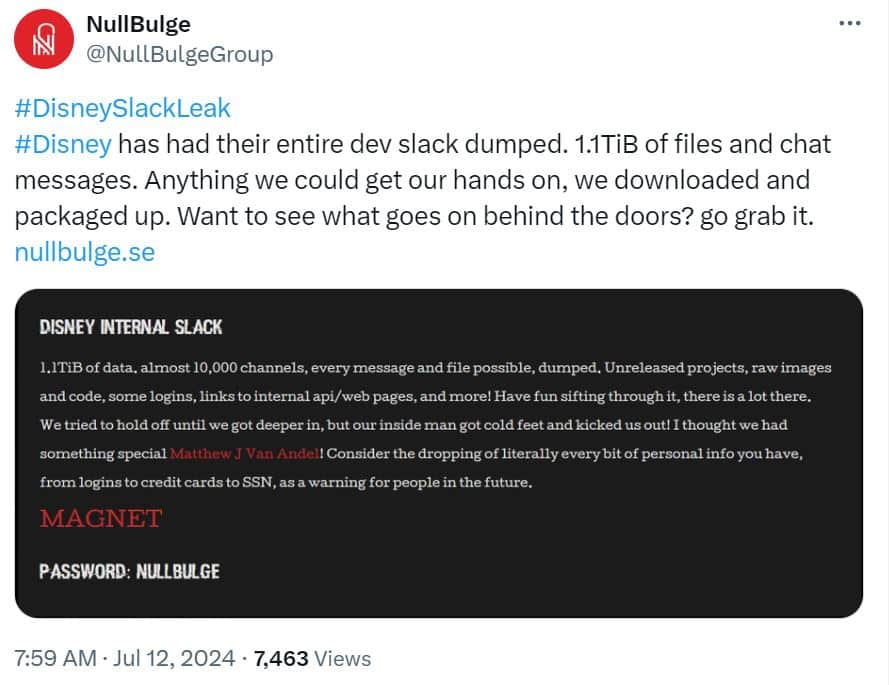
The embedded files were named after prominent AI companies, OpenAI and Anthropic. Eventually, he gained access to private Disney Slack channels and, by May, downloaded 1.1 terabytes of confidential data.
After posing as a hacktivist and receiving no response, Kramer publicly released the stolen Disney material and employee’s personal banking, medical, and other private details. Court documents revealed that at least two other individuals had also installed Kramer’s malicious software, granting him unauthorized access to their computers and accounts as well. Kramer is expected to appear in court in the coming weeks.
The consequences of these breaches range from potential harm to customers and reputational damage to the significant compromise of sensitive data, highlighting the need to implement stronger cybersecurity measures, including stringent access controls, continuous monitoring of network activity, and employee training on identifying and avoiding social engineering tactics.
HackRead