Hacker Accesses Millions of IMDataCenter Records from Exposed AWS Bucket

Cybersecurity researcher Jeremiah Fowler discovered a major data leak at a Florida-based data solutions provider, IMDataCenter. The leak exposed a massive database containing personal details of users and client companies.
The misconfigured database, with CSV and PDF files, contained a staggering 38GB of information from 10,820 records and was left wide open on the internet without any password protection or encryption.
This leak is particularly alarming because of the type of data exposed. The files contained a vast amount of personally identifiable information (PII), including names, physical addresses, phone numbers, and email addresses. What makes this data dangerous is that it also had sensitive personal details like lifestyle information and home or vehicle ownership.
This valuable, verified information is typically used by IMDataCenter to help clients in various industries, from healthcare and insurance to political campaigns, with their marketing efforts.
The scale of the company’s operation is extensive, with its data library containing details on over 260 million individuals and 600 million email addresses. In the wrong hands, however, this data becomes a perfect tool for criminals.
“With each CSV document containing the data of thousands of individuals, it is difficult to calculate the total number of those who may have potentially had their data exposed,” Fowler noted in the blog post.



The exposure of such a detailed dataset poses significant risks for the victims. The personal details can be used to launch highly convincing phishing scams and other fraudulent schemes.
For example, a scammer could use a person’s verified home address and phone number to make a fraudulent call or email seem more legitimate. This breach could also lead to an increased risk of identity theft and financial crimes as criminals build detailed profiles on their targets.
Upon discovering the exposed data, Fowler sent a “responsible disclosure notice” to IMDataCenter. The database was quickly restricted from public access and is no longer available. A company representative responded, stating, “Data security is really important to us too and really appreciate you sharing this information with us. We are working to secure the information ASAP.”
While the records appeared to belong to IMDataCenter, it remains unknown if the company directly managed the database or if a third-party contractor was responsible.
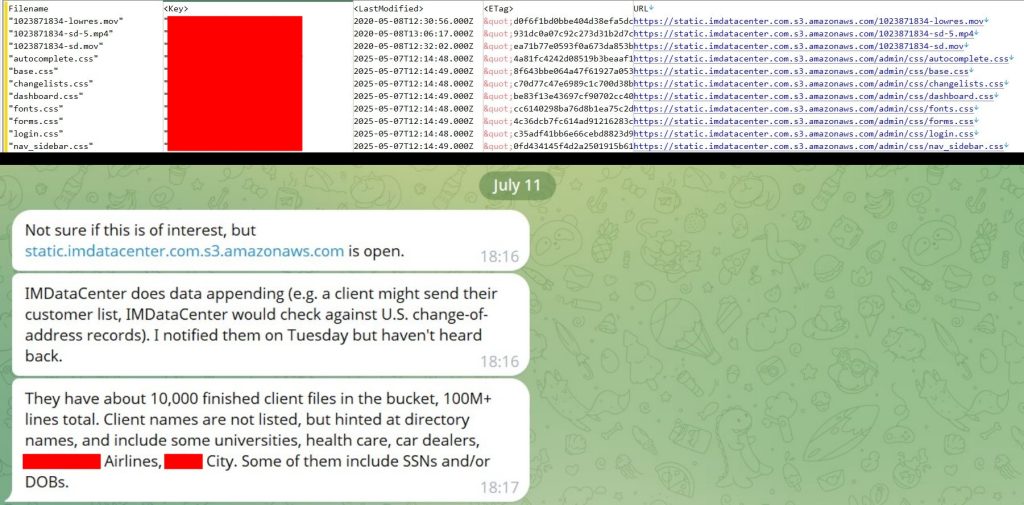
However, There’s More to The Story…In mid-July 2025, Hackread.com was contacted by a BreachForum user known as ThinkingOne. They claimed to have accessed IMDataCenter’s AWS bucket, which held around 40 GB of data, expanding to roughly 75 GB once uncompressed, with new records being added daily.
ThinkingOne said they had tried to alert IMDataCenter after spotting the leak but never received a response. Eventually, they downloaded all the data available at that time, which included 20 million unique email addresses and 37 million phone numbers.
They also shared that they were able to extract files revealing the names of some of IMDataCenter’s clients, along with sensitive data such as Social Security Numbers (over 50,000) and dates of birth. While the clients weren’t directly named, folder and file names pointed to organizations like airlines, healthcare providers, universities, car dealerships and others.
Hackread.com has chosen not to name these clients to protect their privacy. However, this does not change the fact that IMDataCenter’s exposed data has already been downloaded by at least one third party.
It’s also important to mention that ThinkingOne is known for previous data-related leaks, including the release of 2.8 billion X (formerly Twitter) user profile data in March 2025.
HackRead




